tcpdump shows the unscaled window size. It is important to note that the value of wscale is not the value by which to multiply, it is the bits that are set on the scaling factor, as it uses binary math. An example will hopefully make this clearer.
If the wscale = 8, then that means all eights bits are set, so we must multiply the win size in subsequent packets by 256 (yes, I know it should be 255, but this is the math 😉 ). If the wscale = 7, we must multiply it by 128, if it is 6, we must multiply 64, etc.
[root@CMHLDORLGRD01 ~]# cat windowsize.awk
{
if ($0 ~ "wscale" && $8 == "win") {
i=0
while (++i <= NF) {
if ($i ~ "wscale") {
split($12,t,",");
scale = t[1]
}
}
}
else if($0 ~ "wscale" && $8 == "ack") {
i=0
while (++i <= NF) {
if ($i ~ "wscale") {
gsub(">","",$(i + 1));
scale = $(i + 1)
}
}
}
else if($0 ~ "win") {
j=0
while (++j <= NF) {
if ($j == "win") {
print rshift(256,8-scale),scale,$(j+1)*rshift(256,8-scale),$0
}
}
}
}
[root@CMHLDORLGRD01 ~]# tcpdump -r rpmissue201609052018.pcap | awk '$3 ~ "clientcomputer"' | awk -f windowsize.awk | tail -10
reading from file rpmissue201609052018.pcap, link-type EN10MB (Ethernet)
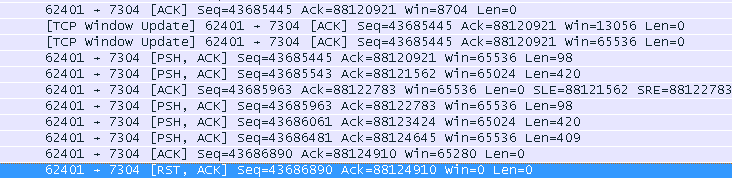
256 8 13056 20:33:51.492651 IP clientcomputer.62401 > 172.27.26.65.7304: . ack 88120921 win 51
256 8 65536 20:33:51.493518 IP clientcomputer.62401 > 172.27.26.65.7304: . ack 88120921 win 256
256 8 65536 20:33:56.848880 IP clientcomputer.62401 > 172.27.26.65.7304: P 43685445:43685543(98) ack 88120921 win 256
256 8 65024 20:33:56.895281 IP clientcomputer.62401 > 172.27.26.65.7304: P 43685543:43685963(420) ack 88121562 win 254
256 8 65536 20:33:57.103377 IP clientcomputer.62401 > 172.27.26.65.7304: . ack 88122783 win 256
256 8 65536 20:34:37.307916 IP clientcomputer.62401 > 172.27.26.65.7304: P 43685963:43686061(98) ack 88122783 win 256
256 8 65024 20:34:37.315096 IP clientcomputer.62401 > 172.27.26.65.7304: P 43686061:43686481(420) ack 88123424 win 254
256 8 65536 20:34:37.323054 IP clientcomputer.62401 > 172.27.26.65.7304: P 43686481:43686890(409) ack 88124645 win 256
256 8 65280 20:34:37.537044 IP clientcomputer.62401 > 172.27.26.65.7304: . ack 88124910 win 255
256 8 0 20:36:09.089412 IP clientcomputer.62401 > 172.27.26.65.7304: R 43686890:43686890(0) ack 88124910 win 0
[root@CMHLDORLGRD01 ~]#
Notice when the same file is run through wireshark, the win sizes match. Right click the image and select open in new window to see it in a more usable format…